Oracle EBS SSO (Single Sign-on) Options and Setup Guide
Learn about Oracle EBS SSO (Options and Setup) with a walk-through video to set up Oracle EBS SSO in 10 minutes. This does not require Oracle Access Manager, Oracle IDCS, or OID, or another SSO server. EBS SSO can be enabled with Active Directory, ADFS, Azure AD, PING, etc. (LDAP or SAML Identity Providers SSO) directly on EBS Server.
What is Oracle EBS SSO?
By default, Oracle E-business Suite(EBS) authenticates users with FND_USER table internally, and this native authentication is known as EBS Local Authentication. As Single Sign-On (SSO) became popular, most organizations prefer to configure SSO for Oracle EBS, and enable logins with SSO credentials instead of the EBS local passwords. So, Oracle EBS SSO simply refers to SSO configuration in Oracle EBS 11i, R12.1, and R12.2.
Oracle EBS SSO is highly recommended for Improved Oracle EBS Security and Better User experience. SSO is a mandatory requirements for IT Security Audits in Oracle e-Business Suite.
Oracle EBS SSO is traditionally enabled with Oracle Access Manager – OAM and Oracle Internet Directory – OID. Prior to Oracle Access Manager (OAM), Oracle 10g Single Sign On (OSSO 10g) had been the traditional Single Sign On options for Oracle EBS from 11i to R1.1. Oracle EBS 12.2 does not support OSSO 10g any more, and it needs either OAM or modern SSO solutions such as Oracle Identity Cloud Services (IDCS) or SSOGEN.
Why is Oracle EBS SSO important?
Users don’t have to remember dozens of passwords for Oracle e-Business Suite – 11i, 12.1, and 12.2.
Weak passwords in Applications are no longer allowed. Welcome123 and Oracle123 are the most popular weak passwords in Oracle EBS.
Access to Oracle EBS is terminated instantly, when an employee/contractor leaves. This is a requirement Audit requirement.
What is an Alternative SSO for EBS?
As traditional SSO solutions are not only expensive, but also complex in nature, and the typical SSO implementation takes about 6 months. An alternative SSO solution for Oracle EBS is SSOGEN, which is implemented under 10 minutes.
SSOGEN is a modern, and NextGen Single Sign On solution that offers many benefits, including free Multi Factor Authentication (MFA), and it integrates with about 300 SSO solutions in the market.
SSOGEN can either authenticate directly with LDAP servers such as Microsoft Active Directory or delegate authentication to your enterprise SSO solutions such as Azure AD, Okta, OneLogin, etc.
Unique Proposition
Unique Solution
Cost Savings
Deployed in Minutes
Exceptional Support
Is SSOGEN Oracle Certified?
Oracle EBS SSO: LDAP Authentication Options
EBS SSO – SSOGEN configuration supports Windows Native Authentication – WNA, Kerberos, Desktop Authentication (Zero Touch SSO), which enables User to access Oracle EBS without having to explicitly login to EBS. Desktop Authentication uses Network/Domain Login for Authentication. Kerberos is still secure and convenient for the users.
In addition to LDAP SSO, SSOGEN also performs multi factor authentication for Oracle EBS for critical environments. Here is a quick list of compatible LDAP Directory Servers for Oracle EBS.
Oracle EBS SSO: Delegated SSO Authentication Options
SSOGEN supports SSO Gateway, SAML Gateway, and OpenID Connect Gateway Solutions. With SSO Gateway, EBS SSO authenticates with CA Siteminder, IBM Tivoli Access Manager – TAM, Oracle Access Manager – OAM authentication to Oracle EBS.
In addition to delegating the authentication to the other SSO systems, SSOGEN is capable of adding multi factor authentication – MFA for Oracle EBS on top of the delegated SSO Auth.
How to configure Oracle EBS SSO?
Here are the high level steps to enable SSO in Oracle EBS (for Azure AD use case):
- Apply EBS AccessGate Patches, if EBS version is lower than 12.2.4.
- Clean up prior SSO registration (if any): $ ./ ssogen cleanup
- Deploy EBS AccessGate: $ ./ ssogen deployag
- Configure SSO in EBS: $ ./ssogen reg
- Add SSOGEN App in Azure AD – Enterprise Applications
- Copy the Azure AD App metadata to EBS and restart EBS services
#1 Apply EBS AccessGate Patches
Oracle EBS SSO Integration is detailed here with step by step instructions. If this is the first time enabling SSO on EBS, the following patches need to be applied. Also, make sure that FS Clone is complete and online patching cycle is NOT active.
| Patch Name | Patch Number | Description |
| R12.2 EBS Patch | 20735848 | |
| EBS AccessGate | 24008856 | Check 2202932.1 for the latest patch |
- SSOGEN Support team sends out customer specific scripts for the registration. Please upload ssogen.zip and ssogen_modules.zip to $NE_BASE/sso, and unzip ssogen.zip
- Oracle e-Business Suite AccessGate – EAG: fndauth.war deployment is now part of 12.2 WebLogic Domain itself, and it deployed to oaea_server1.
- SSO Registration: Enable SSO on all Web Nodes
- If there are DMZ/iSupplier nodes, please repeat the above step, with function dmzreg
- Bounce all EBS Services on Web Tiers and test the SSO logins.
- For deploying access gate, you may follow Oracle standard, adProvisionEBS.pl ebs-create-oaea_resources. However, deployag script does call the same script for your convenience
#2 Clean up prior SSO registration (if any)
Run Cleanup to register previous SSO/LDAP references in the databasae, FND_USER_PREFERENCES..etc
$ cd $NE_BASE/sso $ unzip ssogen.zip $ ./ssogen cleanup
#3 Deploy Oracle EBS AccessGate
$ ./ssogen deployag
If there are multiple Web Nodes configured for High Availability, the above script has to be run on all Web Tiers, with the node no# matching oaea_server#. For example:
Node1: ./ssogen deployag node1 Node2: ./ssogen deployag node2
Please use -managedsrvport flag to specify port number explicitly. For example: .
/ssogen .. deployag node1 -managedsrvport=6821
If deploag fails for any reason, please run undeployag to clean up the previous deployment, and run deployag to complete the deployment. This post-clone step may be necessary in some cases.
./ssogen undeployag ./ssogen deployag
#4 EBS SSO Registration
SSO Registration is the process in which EBS URL is registered with SSO for logins.
$ ./ssogen reg
Restart all Oracle EBS Services and test SSO Login at /OA_HTML/AppsLogin
EBS Local Logins continue to work with the URL: /OA_HTML/AppsLocalLogin.jsp
Non-SSO (Non-LDAP/AD) users such as SYSADMIN can still login through the Local Login URL: /OA_HTML/AppsLocalLogin.jsp
#5 Add SSOGEN App in Azure AD – Enterprise Applications
Search SSOGEN Gallery App by SSOGEN keyword, Add App, and Configure EBS URLs from SSOGEN Reg command, and download the app metadata
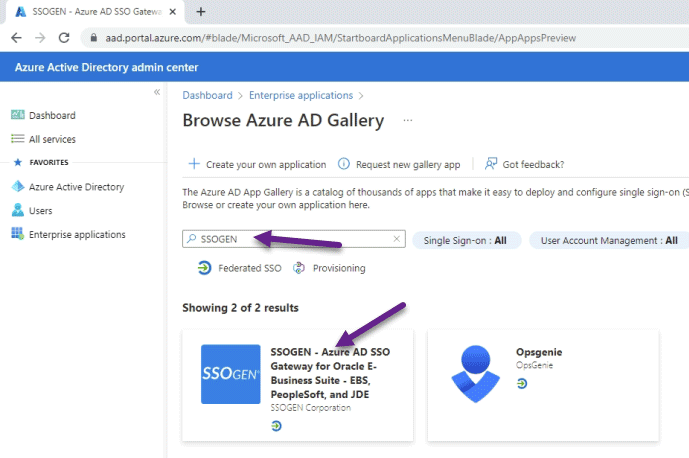
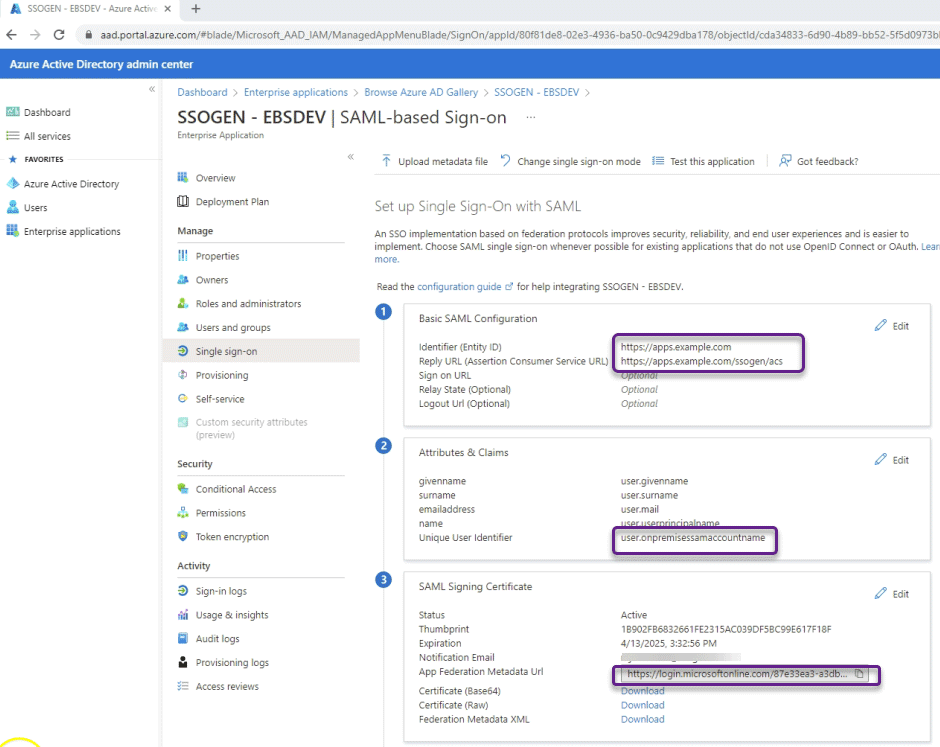
#6 Copy App Metadata and Restart EBS Services
Copy the Azure AD – App Metadata URL to ssogen folder as idp.xml & Restart EBS Services with adstpall.sh and adstrtal.sh
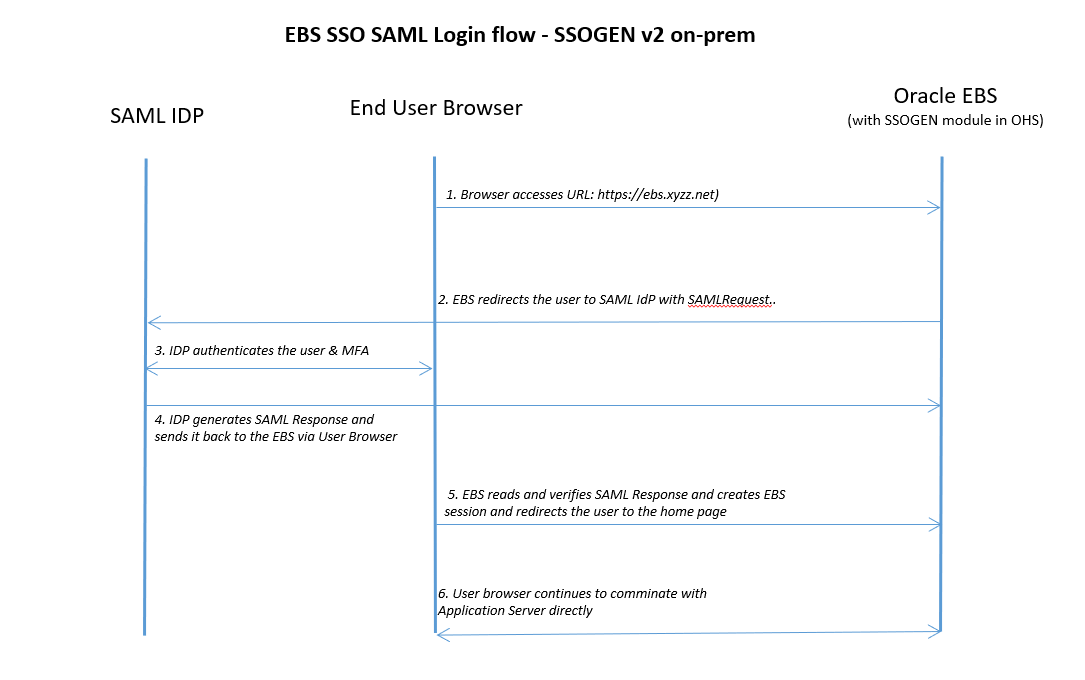
Oracle EBS SSO Login Flow
- User accesses EBS URL in the browser
- EBS redirects to SAML IdP with SAML Request
- SAML IdP/ADFS performs the authentication either by collecting username and password inputs or by network login/Kerberos, based on its configuration
- Once SAML IdP/ADFS successfully performed the authentication, it redirects the user to EBS with a SAM Response, which includes a signature, NameID, etc.
- EBS Server reads SAML Response and creates its own EBS session
- EBS identifies the FND Responsibilities (Authorizations)
- User lands in EBS Home Page
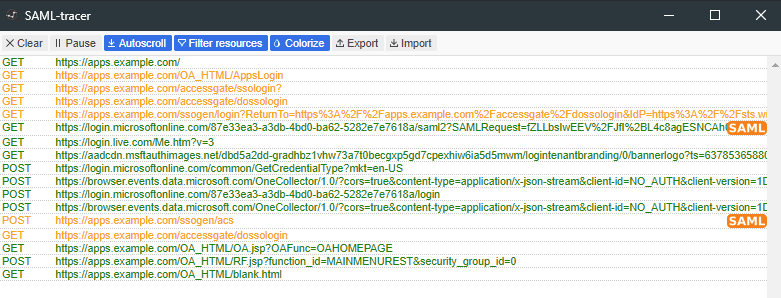
Oracle EBS SSO Login Trace with SAML Tracer and HTTP requests
Lets take a look at the EBS SSO login trace with SAML Tracer and HTTP requests:
- https://apps.example.com is the EBS URL here
- https://login.microsoftonline.com is the SAML IdP URL in this case
- The first SAML request is the SAMLRequest, and the second is the SAML Response
- There is no third party between EBS and SAML IdP
- Browser acts as a channel between the EBS and SAML IdP
- No direct communication between EBS Server to SAML IdP
Oracle EBS SSO Profile Options
Oracle EBS Single Sign On Profiles that matter most for Oracle EBS SSO Integration are shown below.
| EBS Release | 12.2.x |
| EBS SSO URL | https://apps.example.com/OA_HTML/AppsLogin |
| EBS Backdoor/Local Login | https://apps.example.com/OA_HTML/AppsLocalLogin.jsp |
| Application Authenticate Agent | https://apps.example.com/accessgate/ |
| Applications SSO Type | SSWA w/SSO |
| Applications SSO Auto Link User | Enabled |
| Application SSO LDAP Synchronization | Disabled |
| Applications Override SSO Server Language | Override SSO Server Language |
| Applications SSO User Creation and Updation Allowed | Enabled |
| Applications SSO Login Types | BOTH |
Oracle EBS SSO: Troubleshooting and Fixes
ORA-20001: Unable to call fnd_ldap_wrapper.create_user due to following reason: Oracle Internet Directory is not registered correctly.
Solution:
Application SSO LDAP Synchronization profile may impact user creation process.
Please make sure that system profile Application SSO LDAP.
Synchronization is set to DISABLED. Also, ensure other SSO profiles are set as suggested above and that the system is not previously registered with another sso such as Oracle OAM, Oracle SSO, and Oracle OID/OUD. Please cleanup SSO preferences as documented above.
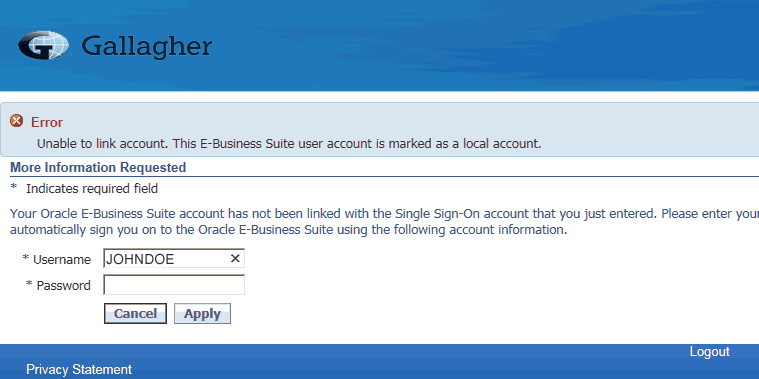
Error: Unable to link account. This E-Business Suite user account is marked as a local account.
More Infromation Requested
*Indicates required field
Your Oracle E-Business Suite account has not been linked with the Single Sign-On account that you just entered. Please enter you Oracle E-Business Suite information. The next time you sign on with your Single Sign-On account, it will automatically sign you on to the Oracle E-Business Suite using the following account information.
Solution:
Applications SSO Login Types is set to Local for this user, 502662611. Profile “Applications SSO Login Types” should be set to either BOTH or SSO for SSO login to work. This profile is typically set to BOTH at Site Level, and it’s NOT set at the user level.
“Applications SSO Login Types” is typically set to Local to reset EBS Local password (in FND_USER table). If this profile “Applications SSO Login Types” is set to BOTH, Password change is not allowed. User Password field is greyed out in User Form. If this is the case, after password is reset, remove the user level value for this profile.
Your Oracle E-Business Suite account has not been linked with the Single Sign-On account.
Your Oracle E-Business Suite account has not been linked with the Single Sign-On account.
More Information Requested:
Your Oracle E-Business Suite account has not been linked with the Single Sign-On account that you just entered. Please enter your Oracle E-Business Suite information. The next time you sign on with your Single Sign-On account, it will automatically sign you on to the Oracle E-Business Suite using the following account information.
This Autolink page is thrown when EBS can not find the user name by the GUID sent by the SSO Server. EBS instance has previously been registered with another SSO or user has manually linked to another user by submitting another user name and password in this page. SSS User SSO7 has got previous GUID value in FND_USER table. This user has to be unlinked, by updating GUID null, which enables EBS Autolink feature to populate the right GUID value during the next SSO login.
SQL> select user_name,end_date,user_guid from fnd_user where user_name='SSO7'; USER_NAME END_DATE USER_GUID SSO7 B31318AC7A93622BC050A3C0250108F2 SQL>update fnd_user set user_guid = null where user_name='SSO7' ; 1 row updated. SQL>commit ; Commit complete. SQL> select user_name,end_date,user_guid from fnd_user where user_name='SSO7' ; USER_NAME END_DATE USER_GUIDSSO7
Please suggest the user to re-try the sso login
SQL> select user_name,end_date,user_guid from fnd_user where user_name='SSO7' ; USER_NAME END_DATE USER_GUID SSO7 B34C930A342BBE63D140A8C046014980
Verify Oracle EBS SSO Profiles
The following profiles are very important for EBS SSO Functionality:
select fpot.user_profile_option_name, fpov.profile_option_value,fpov.last_update_date,fu.user_name from apps.fnd_profile_options fpo, apps.fnd_profile_options_tl fpot, apps.fnd_profile_option_values fpov, apps.fnd_user fu where fpo.profile_option_id = fpov.profile_option_id and fpov.level_id=10001 and fpov.last_updated_by=fu.user_id and fpo.profile_option_name=fpot.profile_option_name and fpot.language='US' and fpo.profile_option_name in( 'APPS_FRAMEWORK_AGENT', 'APPS_AUTH_AGENT', 'APPS_SSO', 'APPS_SSO_LOCAL_LOGIN', 'APPS_SSO_AUTO_LINK_USER', 'APPS_SSO_ALLOW_MULTIPLE_ACCOUNTS', 'APPS_SSO_USER_CREATE_UPDATE', 'APPS_SSO_LDAP_SYNC', 'APPS_SSO_LINK_TRUTH_SRC', 'FND_OVERRIDE_SSO_LANG') order by 1;
Make sure that the output matches to the following profile values:
SQL> / Application Authenticate Agent http://demoebs.ssogen.com:8000/accessgate 10-APR-17 ANONYMOUS Application Framework Agent http://demoebs.ssogen.com:8000 10-APR-17 ANONYMOUS Application SSO LDAP Synchronization N 20-MAY-17 ANONYMOUS Applications Override SSO Server Language ENABLED 26-AUG-16 SYSADMIN Applications SSO Allow Multiple Accounts N 19-JUL-06 ORACLE12.2.0 Applications SSO Auto Link User Y 26-AUG-16 SYSADMIN Applications SSO Linking Source of Truth OID 19-JUL-06 ORACLE12.2.0 Applications SSO Login Types BOTH 26-AUG-16 SYSADMIN Applications SSO Type SSWA_SSO 05-JUN-17 ANONYMOUS Applications SSO User Creation and Updation Allowed Y 19-JUL-06 ORACLE12.2.0 10 rows selected. SQL>
Check EBS User for end date
select user_name,end_date,user_guid from fnd_user where user_name='&EBS_SSO_USER_NAME';
When in doubt, update the GUID to null so that it gets set during the SSO login:
update fnd_user set user_guid=null where user_name='&EBS_SSO_USER_NAME' ;
Check User Level profile options for any suspicious profiles:
select fpot.user_profile_option_name, fpov.profile_option_value,fpov.last_update_date,fu1.user_name from apps.fnd_profile_options fpo, apps.fnd_profile_options_tl fpot, apps.fnd_profile_option_values fpov, apps.fnd_user fu,apps.fnd_user fu1 where fpo.profile_option_id = fpov.profile_option_id and fpov.level_id=10004 and fpov.level_value=fu.user_id and fpov.last_updated_by=fu1.user_id and fpo.profile_option_name=fpot.profile_option_name and fpot.language='US' and fu.user_name='&EBS_SSO_USER_NAME' order by 1;
Oracle e-Business Suite AccessGate – EAG Troubleshooting
- Verify the AccessGate version from http://demoebs.ssogen.com:8000 /accessgate/style/EbusinessAccessGate.class
- Check 2202932.1 for the latest patch if any AccessGate issues are observed
- Enable Debug at the AccessGate and restart oaea_serverx
cat <<EOC > /tmp/oaealog handlers=java.util.logging.FileHandler .level= ALL java.util.logging.FileHandler.pattern = /tmp/fndauth%u.log java.util.logging.FileHandler.limit = 10000000 java.util.logging.FileHandler.count = 1 java.util.logging.FileHandler.level = FINE java.util.logging.FileHandler.formatter = java.util.logging.SimpleFormatter oracle.apps.fnd.ext.common.level=FINE oracle.apps.fnd.ext.common.server.level=FINE EOC cat <<EOC2 >> $INST_TOP/appl/admin/oaea_wls.properties LOG_CONFIG_FILE=/tmp/oaealog EOC2
For additional info, refer to How To Collect E-Business Suite 12.2 AccessGate LogFiles (Doc ID 1683163.1)
HTTP 400 – Bad Request Errors after enabling SSO
As SSO adds many cookies, you would see HTTP 400 in R12.1 & R12.2 when the apache request limits are reached.
Please suggest the customer to set the following limits in $CONTEXT_FILE , run autoconfig, and restart all services.
R12.2:
<limitrequestfieldsize oa_var="s_limitrequestfieldsize">16384</limitrequestfieldsize>
<limitrequestfields oa_var="s_limitrequestfields">128</limitrequestfields>
<limitrequestbody oa_var="s_limitrequestbody">0</limitrequestbody>
<limitrequestline oa_var="s_limitrequestline">16384</limitrequestline>
R12.1:
<limitrequestfieldsize oa_var="s_limitrequestfieldsize">8190</limitrequestfieldsize>
<limitrequestfields oa_var="s_limitrequestfields">64</limitrequestfields>
<limitrequestbody oa_var="s_limitrequestbody">0</limitrequestbody>
<limitrequestline oa_var="s_limitrequestline">8190</limitrequestline>
Related Oracle Notes:
- EBS requests fail with “Size of a request header field exceeds server limit” [ID 1370626.1]
- Lengthy Configurator URL : CZ Does Not Launch [ID 1374444.1]
- Url Causes Http 400 Error [ID 1374260.1]
EBS R12 timeout problems
Check the following timeout variables in $CONTEXT_FILE:
- s_sesstimeout
- s_oc4j_sesstimeout
- s_forms_time
- s_ohstimeout
Check the following EBS profile options
- ICX:Session Timeout
- ICX: Limit connect
- ICX: Limit time
Refer to the following Oracle Notes for more info:
- R12: Forms Timeout More Than 2 Hrs Is Not Working After R12 Upgrade [ID 734077.1]
- How to Change User Session Timeout in e-Business Suite R12 [ID 1067115.1]
- User Sessions Get Timed Out Before Idle Time Parameter Values Are Reached [ID 1306678.1]
- Self-Service Pages Are Failing After Changing the s_oc4j_sesstimeout [ID 780612.1]
- How AutoConfig sets ICX: Session Timeout [ID 307149.1]
- 11i/R12 How to Debug “Transaction Context Is Lost” or “You are trying to access a page that is no longer active” [ID 456906.1]
- Random error Your login session has expired when using Load Balancing [ID 387306.1]
Load Balancer URL Redirection issues
The following context variables should be set correctly for the load balancer URL to function:
- s_webentryhost
- s_webentrydomain
- s_active_webport
- s_webentryurlprotocol
- s_url_protocol
- s_local_url_protocol
- s_login_page
- s_enable_sslterminator
- s_external_url
SSL Termination/Redirection issues
egrep ‘s_web|s_active_webport|s_login_page|s_enable_sslterminator|s_url_protocol|s_local_url_protocol|s_login’ $CONTEXT_FILE egrep ‘s_web’ $CONTEXT_FILE
When SSL is terminated at the load balancer, the following values are needed in EBS:
- s_webentryhost=demoebs
- s_webentrydomain=ssogen.com
- s_webentryurlprotocol=https
- s_active_webport=443
- s_enable_sslterminator= { remove # }
- s_login_page=https://demoebs.ssogen.com:443/OA_HTML/AppsLogin
- s_external_url=https://demoebs.ssogen.com:443
Oracle EBS – SSO Login throws HTTP 500 after authentication
Oracle e-Business Suite EBS AccessGate – EAG Log files show: java.lang.NoClassDefFoundError: oracle/ias/cache/ObjectNotFoundException
<26-Oct-2018 17:06:34 o'clock BST> <Error> <ServletContext-/ebsauth_payptt> <BEA-000000> <Context intialization failed
java.lang.NoClassDefFoundError: oracle/ias/cache/ObjectNotFoundException
at oracle.apps.fnd.ext.sso.FndSsoConfigListener.contextInitialized(Unknown Source)
at weblogic.servlet.internal.EventsManager$FireContextListenerAction.run(EventsManager.java:481)
at weblogic.security.acl.internal.AuthenticatedSubject.doAs(AuthenticatedSubject.java:321)
at weblogic.security.service.SecurityManager.runAs(SecurityManager.java:120)
at weblogic.servlet.internal.EventsManager.notifyContextCreatedEvent(EventsManager.java:181)
Truncated. see log file for complete stacktrace
Caused By: java.lang.ClassNotFoundException: oracle.ias.cache.ObjectNotFoundException
at weblogic.utils.classloaders.GenericClassLoader.findLocalClass(GenericClassLoader.java:297)
at weblogic.utils.classloaders.GenericClassLoader.findClass(GenericClassLoader.java:270)
at weblogic.utils.classloaders.ChangeAwareClassLoader.findClass(ChangeAwareClassLoader.java:64)
at java.lang.ClassLoader.loadClass(ClassLoader.java:425)
at java.lang.ClassLoader.loadClass(ClassLoader.java:358)
Truncated. see log file for complete stacktrace
>
Reason: EAG WebLogic Domain does not have JRF (Java Required Files) enabled during the initial creation. oracle/ias/cache libraries are included in Oracle JRF Jar files.
Solution: Recreate the WebLogic Domain with JRF included.
Oracle iSupplier DMZ Configuration – SSO Login is not working for Oracle iSupplier DMZ
Make sure that EBS DMZ is properly set up, as documented in Oracle E-Business Suite R12 Configuration in a DMZ (Doc ID 380490.1)
1. sqlplus apps/apps@/patch/115/sql/txkChangeProfH.sql SERVRESP
2. Set system profile Node Trust Level to External at DMZ Node level
3. Check the context values in DMZ Context file and run auto config.
s_webentryhost=dmz
s_webentrydomain=ssogen.com
s_webentryurlprotocol=https
s_active_webport=443
s_enable_sslterminator= { remove # ; if SSL is terminated in load balancer}
s_login_page=https://dmz.ssogen.com:443/OA_HTML/AppsLogin
s_external_url=https://dmz.ssogen.com:443
4. Verify the following profile options for the products installed in EBS:
Oracle iSupplier
POS: External URL
POS: Internal URL
Oracle Sourcing Supplier
PON: External Applications Framework Agent
PON: External login URL
Oracle iProcurement
Self Registered Employee Default Responsibility
Self Registered New User Default Responsibility
5. Verify Hierarchy Type for the following profiles. Hierarchy type should be properly set by txkChangeProfH.sql SERVRESP from the first step.
|
User Profile Name
|
Internal Name
|
|---|---|
| 1. Applications Web Agent | APPS_WEB_AGENT |
| 2. Applications Servlet Agent | APPS_SERVLET_AGENT |
| 3. Applications JSP Agent | APPS_JSP_AGENT |
| 4. Applications Framework Agent | APPS_FRAMEWORK_AGENT |
| 5. ICX:Forms Launcher | ICX_FORMS_LAUNCHER |
| 6. ICX: Oracle Discoverer Launcher | ICX_DISCOVERER_LAUNCHER |
| 7. ICX: Oracle Discoverer Viewer Launcher | ICX_DISCOVERER_VIEWER_LAUNCHER |
| 8. Applications Help Web Agent | HELP_WEB_AGENT |
| 9. Applications Portal | APPS_PORTAL |
| 10. BOM:Configurator URL of UI Manager | CZ_UIMGR_URL |
| 11. QP: Pricing Engine URL | QP_PRICING_ENGINE_URL |
| 12. TCF:HOST | TCF:HOST |
OAEA error message after 12.2.6 upgrade
Problem:
Error message in the browser: URL Validation Failed
URL: /OA_HTML/jsp/fnd/fnderror.jsp?text=Exception+while+updating+user+session.
oracle.apps.fnd.ext.sso.FndSsoException: Exception while updating user session.
at oracle.apps.fnd.ext.sso.FndSsoFilter.doFilter(Unknown Source)
at weblogic.servlet.internal.FilterChainImpl.doFilter(FilterChainImpl.java:60)
at weblogic.servlet.internal.WebAppServletContext$ServletInvocationAction.wrapRun(WebAppServletContext.java:3748)
at weblogic.servlet.internal.WebAppServletContext$ServletInvocationAction.run(WebAppServletContext.java:3714)
at weblogic.security.acl.internal.AuthenticatedSubject.doAs(AuthenticatedSubject.java:321)
at weblogic.security.service.SecurityManager.runAs(SecurityManager.java:120)
at weblogic.servlet.internal.WebAppServletContext.securedExecute(WebAppServletContext.java:2283)
at weblogic.servlet.internal.WebAppServletContext.execute(WebAppServletContext.java:2182)
at weblogic.servlet.internal.ServletRequestImpl.run(ServletRequestImpl.java:1499)
at weblogic.work.ExecuteThread.execute(ExecuteThread.java:263)
at weblogic.work.ExecuteThread.run(ExecuteThread.java:221)
Caused by: java.lang.IllegalArgumentException: Illegal empty string argument
at oracle.apps.fnd.util.PreCondition.assertNotNull(PreCondition.java:109)
at oracle.apps.fnd.util.PreCondition.assertNotNullOrEmpty(PreCondition.java:169)
at oracle.apps.fnd.util.PreCondition.assertNotNullOrEmpty(PreCondition.java:
Cause: EBS has been upgraded to 12.2.6 and latest EAG patch wasn’t applied.
Solution: Issue has been fixed after applying 24008856 and performing undeploy and deploy of accessgate.
Issue# 2: We have seen similar issues, when previous 12.1 SSO registration is not cleaned up before upgrading to 12.2.
In this case, we have to run cleanup or $FND_TOP/bin/txkrun.pl -script=SetSSOReg -removereferences=yes to remove previous SSO/LDAP registration and proceed with SSOGen Registration
How does this profile work? Applications SSO Login Types – APPS_SSO_LOCAL_LOGIN
Problem
After enabling SSO in Oracle EBS, default EBS URL, /OA_HTML/AppsLogin is SSO enabled. Backdoor URL / Local Login for Non-SSO users such as SYSADMIN is still allowed through Local Login URL /OA_HTML/AppsLocalLogin.jsp. However, some of the user logins are not working through Backdoor URL / Local Login URL.
Cause
System Profile, Applications SSO Login Types, APPS_SSO_LOCAL_LOGIN, is set to SSO.
Solution
System Profile, Applications SSO Login Types, APPS_SSO_LOCAL_LOGIN should be set to BOTH or LOCAL for local login to succeed at User Level (for example SYSADMIN). Applications SSO Login Types: LOCAL allows that only Local Logins through /OA_HTML/AppsLocalLogin.jsp. SSO allows SSO logins through /OA_HTML/AppsLogin only. BOTH allows both SSO logins and Local Logins.
Unable to change EBS Password in Password Field in FND User Form – Grayed out
Problem
Unable to set the EBS Local Passwords after enabling SSO. EBS Passwords are typically stored in FND_USER table.
Cause
System Profile, Applications SSO Login Types, APPS_SSO_LOCAL_LOGIN, is set to SSO.
Solution
System Profile, Applications SSO Login Types, APPS_SSO_LOCAL_LOGIN should be set to BOTH or LOCAL to set EBS password at user Level or site level. We recommend BOTH at site level, which allows password changes, and local logins.
Oracle EBS SSO Links
Read more about Oracle EBS SSO Integrations from the following links
Microsoft Active Directory SSO
Radiant Login Directory